
The Security Issues Caused By Misdirected Emails
When we consider the security of our business technology, we often think of scams or phishing e-mails. These get easily shrugged off, as we assume[...]

Introducing…The Facebook Tango
Do you like to dance? Dancing is both a science and an art. The waltz is a beautiful and romantic flowing dance, the foxtrot involves[...]

The Key to Winning the Age Old Battle for Privacy on LinkedIn is…
LinkedIn, the increasingly popular business and employment-focused social networking site is a crucial tool for professionals who are happily employed or still searching for the[...]

Is LinkedIn Premium Really Worth the Splurge?
We know LinkedIn is the most popular ‘social network’ for professionals in a wide variety of industries. It’s filled with fantastic features and functions that[...]

Why Your Network Security in St. Louis Demands an Inside-Outside Threat Defense Strategy
Do you feel the security of your network is “in the bag,” so to speak? Or, is there something left to be desired in terms[...]

Your Strategic Technology Plan for 2018
Have you thought about technology and the role it plays in your company’s success? Strategic Technology Planning bolsters your efforts to establish a competitive advantage[...]

10 Ways to Maximize Amazon’s Alexa for Business
We all wish that we had a personal assistant who would manage all aspects of our lives. Wouldn’t it be great to have someone who[...]
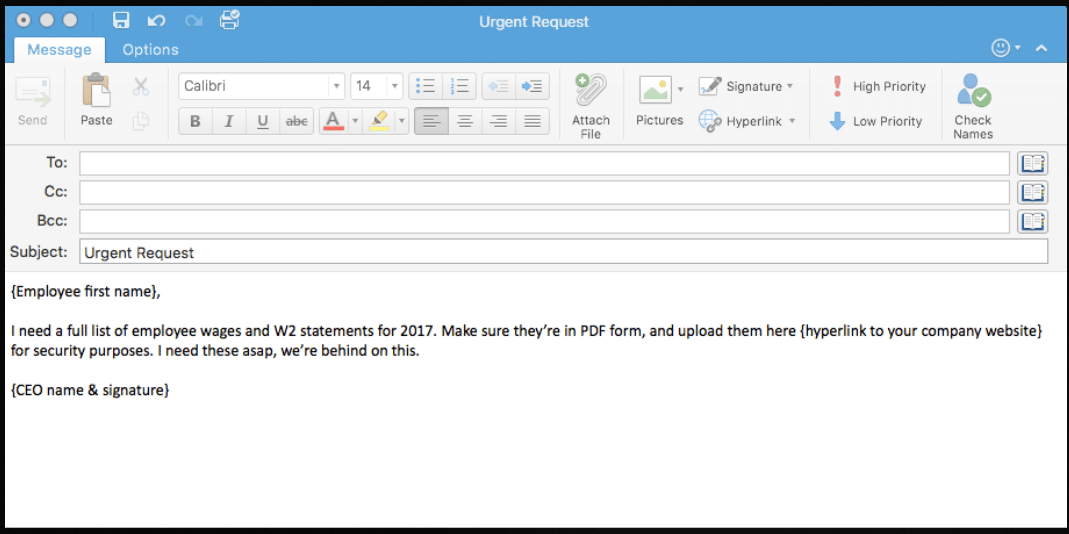
Don’t Wait To Start Training Your Employees To Protect Your Business During W-2 Phishing Season
W-2 Phishing season is about to begin – without the right IT security services, your business will be left vulnerable. You and I know that[...]

Ensure Your Cybersecurity For 2018
Cybersecurity, no matter the size of your business or how many employees you have, is a vital part of today’s business. Everyone in your organization[...]